Make sure you write within the PRE! Also, edit the HTML! NOT DIRECTLY in this editor!!!!
@article{Liaskos.2010,
author = {Liaskos, C. and Petridou, S. and Papadimitriou, G.},
year = {2010},
title = {{T}owards {R}ealizable, {L}ow-{C}ost {B}roadcast {S}ystems for {D}ynamic {E}nvironments},
pages = {383--392},
volume = {19},
number = {2},
journal = {IEEE/ACM Transactions on Networking},
url = {./files/jrn/TNET.pdf},
doi = {10.1109/TNET.2010.2062534},
html = {./?Publications___1-Page_reviews___TNET&normal},
articleabstract={A main design issue in a wireless data broadcasting system is to choose between push-based
and pull-based logic: the former is used as a low cost solution, while the latter is preferred when performance
is of utmost importance. Therefore, the most significant advantage of a push system is the minimal cost.
This fact implies that hardware limitations do exist in the case of push systems. As a consequence, every
related proposed algorithm should primarily be cost-effective. This attribute however has been overlooked in
related research. In this paper, popular broadcast scheduling approaches are tested from an implementation
cost aspect and the results render them only conditionally realizable. Moreover, a new, cost-effective,
adaptivity-oriented schedule constructor is proposed as a realistic, minimal cost solution.},
keypoints={The minimization of the size of the broascast schedule yields:
Minimal scheduling compexity.
Minimal caching needs at the broadcast stations (beacons).
Minimal required communication between the scheduling service and the remote data sites.
*The minimization of the schedule size does not affect the offered QoS level.}
}
@article{TIFS.2018,
author = {Liaskos, C. and Ioannidis, S.},
year = {2018},
title = {Network Topology Effects on the Detectability of Crossfire Attacks},
journal = {IEEE Transactions on Information Forensics and Security},
url = {./files/jrn/TIFS18.pdf},
doi = {10.1109/TIFS.2018.2799425},
articleabstract = {New strains of Distributed Denial-of-Service
(DDoS) attacks have exhibited potential to disconnect communication
networks, even cutting off entire countries from
the Internet. The Crossfire is a new, indirect DDoS linkflooding
attack, which masks itself as natural congestion,
making it very hard to counter. Several studies have
proposed online attack detection schemes, whose efficiency
has been shown to vary in different network topologies.
However, the topology/detection relation has been studied
qualitatively, without formal proof or quantification metric.
The present study is motivated by the fact that network
topology changes are generally expensive and slow. Therefore,
network designers should be provided with means of
evaluating the effects of topology modifications to the attack
detection efficiency. The study fills this gap by contributing
a formal proof for the topology-detection efficiency relation,
as well as a novel offline metric that quantifies it. Full
attack prototypes are implemented and evaluated in real
Internet topologies, validating the analytical findings. It
is shown that the novel metric expresses the topologydetection
relation efficiently, while existing and widely-used
metrics do not constitute good choices for this task.}
}
@inproceedings{ISCAS18.2,
author = {Liu, F. and Pitilakis, A. and Mirmoosa, M. and Tsilipakos, O. and Wang, X. and Tasolamprou, A. and Abadal, S. and Cabellos, A. and Alarcon, E. and Liaskos, C. and Kantartzis, N.},
title = {Programmable Metasurfaces: State of the Art and Prospects},
booktitle = {IEEE International Symposium on Circuits {\&} Systems (ISCAS'18) - Special Session},
year = {2018},
articleabstract = {Metasurfaces, ultrathin and planar electromagnetic
devices with sub-wavelength unit cells, have recently attracted
enormous attention for their powerful control over electromagnetic
waves, from microwave to visible range. With tunability
added to the unit cells, the programmable metasurfaces enable
us to benefit from multiple unique functionalities controlled
by external stimuli. In this review paper, we will discuss the
recent progress in the concept of programmable metasurfaces
and elaborate different approaches to realize them, with the
tunability from global aspects, to local aspects, and to software-defined
metasurfaces.},
url = {./files/cnf/ISCAS_2018_progmeta_VisorSurf.pdf}
}
@inproceedings{CAMAD.2,
author = {Liaskos, C. and Tsioliaridou, A. and Ioannidis, S.},
title = {Towards a Circular Economy via Intelligent Metamaterials},
booktitle = {IEEE CAMAD - Special Session},
year = {2018},
articleabstract = {The present study proposes the use of intelligent
metasurfaces in the design of products, as enforcers of circular
economy principles. Intelligent metasurfaces can tune their physical
properties (electromagnetic, acoustic, mechanical) by receiving
software commands. When incorporated within products and spaces
they can mitigate the resource waste caused by inefficient, partially
optimized designs and security concerns. Thus, circular economy and
fast-paced product design become compatible. The study begins by
considering electromagnetic metamaterials, and proposes a complete
methodology for their deployment. Finally, it is shown that the same
principles can be extended to the control of mechanical properties of
objects, exemplary enabling the micro-management of vibrations and heat,
with unprecedented circular economy potential.},
url = {./files/cnf/CAMAD18si.pdf}
}
@inproceedings{SPAWC.2019,
author = {Liaskos, C. and Tsioliaridou, A. and Nie, Shuai and Pitsillides, Andreas and Ioannidis, S. and Akyildiz, I. F.},
title = {An Interpretable Neural Network for Configuring Programmable Wireless Environments},
pages = {1--5},
booktitle = {IEEE SPAWC 2019},
year = {2019},
url = {https://arxiv.org/pdf/1905.02495.pdf}
}
@inproceedings{CS.DCOSS.2019,
author = {Liaskos, C. and Tsioliaridou, A. and {Pitilakis A} and Pyrialakos, G. and Tsilipakos, O. and Tasolamprou, A. and Kantartzis, N. and Ioannidis, S. and Kafesaki, M. and Pitsillides, A. and Akyildiz, I. F.},
title = {Joint Compressed Sensing and Manipulation of Wireless Emissions with Intelligent Surfaces},
pages = {1--6},
booktitle = {IEEE DCOSS 2019, IoT 4.0 Workshop},
year = {2019},
url = {https://arxiv.org/pdf/1904.10670.pdf}
}
@inproceedings{SMACE.2019,
author = {Liaskos, C. and Tsioliaridou, A. and Ioannidis, S.},
title = {Organizing Network Management Logic with Circular Economy Principles},
pages = {1--6},
booktitle = {IEEE DCOSS 2019 -Smart Circular Economy track},
year = {2019}
}
@inproceedings{Dion.2019,
author = {Manessis, D. and Seckel, M. and Liu, F. and Tsilipakos, O. and {Pitilakis A} and Kossifos, K. and Liaskos, C. and Kafesaki, M. and Tretyakov, S. and Georgiou, J. and Ostmann, A. and Aschenbrenner, R. and Schneider-Ramelow, M. and Lang, K.},
title = {High frequency substrate technologies for the realisation of software programmable metasurfaces on PCB hardware platforms with integrated},
booktitle = {EMPC 2019},
year = {2019}
}
@article{Taqwa.2019,
author = {Taqwa, S. and Skitsas, Constantinos and Kouzapas, Dimitrios and Lestas, M. and Soteriou, Vassos and Philippou, Anna and Liaskos, C. and Petrou, Loukas and Georgiou, J. and Pitsillides, Andreas},
year = {2019},
title = {Fault Adaptive Routing in Metasurface Controller Networks},
journal = {Journal of System Architecture (accepted for publication)},
url= {https://arxiv.org/pdf/1810.06329.pdf}
}
@inproceedings{CAMAD.1,
author = {Tsioliaridou, A. and Liaskos, C. and Ioannidis, S.},
title = {BitSurfing: Wireless Communications with Outsourced Symbol Generation},
booktitle = {IEEE CAMAD},
year = {2018},
articleabstract = {Nano-IoT enables a wide range of ground-breaking
technologies, but face implementation challenges due to the extremity
of the scale. Space restrictions pose severe power supply considerations,
to the point where just a few packet transmissions are sufficient to
deplete state-of-the-art supplies. In turn, this translates to difficulties
in developing efficient protocols even for basic operations, such as
addressing and routing. The present work proposes a new network adapter
architecture that can address these challenges. The BitSurfing adapter
does not generate packets and, hence, abolishes the need for the
corresponding transmission circuitry and power consumption. Instead,
it relies on an external symbol generator. The BitSurfing adapter reads
incoming symbols, waiting for intended messages to appear in the symbol
stream. A short (1-bit), low-energy pulse is then emitted to notify
neighboring nodes. BitSurfing adapters are shown to exhibit perpetual
(and even battery-less) operation, ability to operate without medium
access control, while being completely transparent to applications.
Moreover, their operation is event-driven, allowing for clock-less
implementations. The new adapters are evaluated in a simulated multi-hop
nano-IoT network and are shown to offer nearly-perfect packet delivery
rates and practically no collisions, under any congestion level. },
url = {./files/cnf/CAMAD18.pdf}
}
@inproceedings{ISCAS18.1,
author = {Tasolamprou, A. and Mirmoosa, M. and Tsilipakos, O. and Pitilakis, A. and Liu, F. and Abadal, S. and Cabellos, A. and Alarcon, E. and Liaskos, C. and Kantartzis, N. and Tretyakov, S. and Kafesaki, M. and Economou, E. and Soukoulis, C.},
title = {Intercell wireless communication in software-defined metasurfaces},
booktitle = {IEEE International Symposium on Circuits {\&} Systems (ISCAS'18) - Special Session},
year = {2018},
articleabstract = {Tunable metasurfaces are ultra-thin, artificial electromagnetic
components that provide engineered and externally
adjustable functionalities. The programmable metasurface, the
HyperSurFace, concept consists in integrating controllers within
the metasurface that interact locally and communicate globally
to obtain a given electromagnetic behaviour. Here, we address the
design constraints introduced by both functions accommodated
by the programmable metasurface, i.e., the desired metasurface
operation and the unit cells wireless communication enabling
such programmable functionality. The design process for meeting
both sets of specifications is thoroughly discussed. Two scenarios
for wireless intercell communication are proposed. The first
exploits the metasurface layer itself, while the second employs
a dedicated communication layer beneath the metasurface backplane.
Complexity and performance trade-offs are highlighted.},
url = {./files/cnf/ISCAS_2018_intercell_com_VisorSurf.pdf}
}
@inproceedings{nanocom.2017,
author = {Tsioliaridou, Ageliki and Liaskos, Christos and Pitsillides, Andreas and Ioannidis, Sotiris},
title = {A Novel Protocol for Network-controlled Metasurfaces},
booktitle = {ACM NANOCOM'17},
series = {NanoCom '17},
year = {2017},
isbn = {978-1-4503-4931-4},
location = {Washington, D.C.},
pages = {3:1--3:6},
articleno = {3},
numpages = {6},
doi = {10.1145/3109453.3109469},
acmid = {3109469},
publisher = {ACM},
address = {New York, NY, USA},
url = {./files/cnf/NANOCOM17.pdf},
keywords = {electromagnetic nano-networking, metasurfaces, protocol},
abstract = {A recently proposed class of materials, called software-defined metamaterials,
can change their electromagnetic behavior on demand, utilizing a nanonetwork embedded in their structure.
The present work focuses on 2D metamaterials, known as metasurfaces, and their electromagnetically
programmable counterparts, the HyperSurfaces. The particular focus of the study is to propose a
nanonetworking protocol that can support the intended macroscopic functionality of a Hyper-Surface,
such as sensing and reacting to impinging waves in a customizable manner. The novel protocol is
derived analytically, using the Lyapunov drift minimization approach, taking into account nano-node energy,
communication latency and complexity concerns. The proposed scheme is evaluated via simulations,
covering both the macroscopic HyperSurface functionality and the microscopic, nanonetwork behavior.}
}
@inproceedings{conext.2017,
author = {Lakiotakis, Emmanouil and Liaskos, Christos and Dimitropoulos, Xenofontas},
title = {Enabling Ultra-Low Delay Teleorchestras using Software-Defined Networking},
booktitle = {Conext'17 (Student workshop)},
series = {Conext'17},
year = {2017},
location = {Seoul, Korea},
pages = {1--3},
url = {./files/cnf/CONEXT17.pdf},
keywords = {SDN, Latency, Routing},
articleabstract = {Ultra-low delay sensitive applications can afford delay only at the
level of msec. An example of this application class are the Networked Music
Performance (NMP) systems that describe a live music performance by geographically
separate musicians over the Internet. The present work proposes a novel architecture for NMP
systems, where the key-innovation is the close collaboration between the network and
the application. Using SDN principles, the applications are enabled to adapt their
internal audio signal processing, in order to cope with network delay increase.
Thus, affordable end-to-end delay is provided to NMP users, even under
considerable network congestion.}
}
@article{Liaskos2019,
doi = {10.1016/j.adhoc.2018.11.001},
url = {./files/jrn/ADHOC18.pdf},
year = {2019},
month = {may},
publisher = {Elsevier {BV}},
volume = {87},
pages = {1--16},
author = {Christos Liaskos and Shuai Nie and Ageliki Tsioliaridou and Andreas Pitsillides and Sotiris Ioannidis and Ian Akyildiz},
title = {A novel communication paradigm for high capacity and security via programmable indoor wireless environments in next generation wireless systems},
journal = {Ad Hoc Networks},
articleabstract = {Wireless communication environments comprise passive objects
that cause performance degradation and eavesdropping concerns due to anomalous
scattering. This paper proposes a new paradigm, where scattering becomes software-
defined and, subsequently, optimizable across wide frequency ranges. Through the
proposed programmable wireless environments, the path loss, multi-path fading and
interference effects can be controlled and mitigated. Moreover, the eavesdropping
can be prevented via novel physical layer security capabilities. The core
technology of this new paradigm is the concept of metasurfaces, which are planar
intelligent structures whose effects on impinging electromagnetic waves are fully
defined by their micro-structure. Their control over impinging waves has been
demonstrated to span from 1 GHz to 10 THz. This paper contributes the software-
programmable wireless environment, consisting of several HyperSurface tiles
(programmable metasurfaces) controlled by a central server. HyperSurfaces are
a novel class of metasurfaces whose structure and, hence, electromagnetic behavior
can be altered and controlled via a software interface. Multiple networked tiles
coat indoor objects, allowing fine-grained, customizable reflection, absorption
or polarization overall. A central server calculates and deploys the optimal
electromagnetic interaction per tile, to the benefit of communicating devices.
Realistic simulations using full 3D ray-tracing demonstrate the groundbreaking
performance and security potential of the proposed approach in 2.4 GHz and 60 GHz
frequencies.}
}
@inproceedings{pitilakisMETA2018,
title={Software-Defined Metasurface Paradigm: Concept, Challenges, Prospects},
author={Pitilakis, A and Tasolamprou, AC and Liaskos, C and Liu, F and Tsilipakos, O and Wang, X and Mirmoosa, MS and Kossifos, K and Georgiou, J and Pitsilides, A and others},
booktitle={2018 12th International Congress on Artificial Materials for Novel Wave Phenomena (Metamaterials)},
pages={483--485},
year={2018},
organization={IEEE},
url = {./files/cnf/META2018.pdf},
doi = {10.1109/MetaMaterials.2018.8534096},
articleabstract = {HyperSurfaces (HSFs) are devices whose electromagnetic (EM)
behavior is software- driven, i.e., it can be defined programmatically. The key
components of this emerging technology are the metasurfaces, artificial layered
materials whose EM properties depend on their internal subwavelength structuring.
HSFs merge metasurfaces with a network of miniaturized custom electronic controllers,
the nanonetwork, in an integrated scalable hardware platform. The nanonetwork
receives external programmatic commands expressing the desired end-functionality
and appropriately alters the metasurface configuration thus yielding the respective
EM behavior for the HSF. In this work, we will present all the components of the HSF
paradigm, as well as highlight the underlying challenges and future prospects.}
}
@article{eccpe.2018,
author = {Lakiotakis, Emmanouil and Liaskos, Christos and Dimitropoulos, Xenofontas},
title = {Improving NetworkedMusic Performance Systems Using Application-Network Collaboration},
journal = {Elsevier Concurrency and Computation: Practice and Experience},
year = {2018},
pages = {1--24},
url = {./files/jrn/ECCPE.pdf},
keywords = {SDN, Latency, Routing},
articleabstract = {Networked Music Performance (NMP) systems involve musicians
located in different places who perform music while staying synchronized via
the Internet. The maximum end-to-end delay in NMP applications is called Ensemble
Performance Threshold (EPT) and should be less than 25 milliseconds. Due to this
constraint, NMPs require ultra-low delay solutions for audio coding, network
transmission, relaying and decoding, each one a challenging task on its own.
There are two directions for study in the related work referring to the NMP systems.
From the audio perspective, researchers experiment on low-delay encoders and
transmission patterns, aiming to reduce the processing delay of the audio transmission,
but they ignore the network performance. On the other hand, network-oriented
researchers try to reduce the network delay, which contributes to reduced
end-to-end delay. In our proposed approach, we introduce an integration of dynamic
audio and network configuration to satisfy the EPT constraint. The basic idea is that
the major components participating in an NMP system the application and the network
interact during the live music performance. As the network delay increases, the
network tries to equalize it by modifying the routing behavior using Software
Defined Networking principles. If the network delay exceeds a maximum affordable
threshold, the network reacts by informing the application to change the audio
processing pattern to overcome the delay increase, resulting in below EPT
end-to-end delay. A full prototype of the proposed system was implemented
and extensively evaluated in an emulated environment.}
}
@article{Liaskos.2012e,
author = {Liaskos, C. and Papadimitriou, G.},
year = {2012},
title = {{O}ptimal {P}eriodic {S}cheduling {U}nder {M}ultimodel {P}er-{I}tem {C}onstraints in {W}ireless {S}ystems},
pages = {1071--1080},
volume = {42},
number = {6},
journal = {IEEE Transactions on Systems, Man, and Cybernetics},
url = {./files/jrn/TSMCC.pdf},
doi = {10.1109/TSMCC.2012.2190927}
}
@article{Liaskos.2012f,
author = {Liaskos, C. and Xeros, A. and Papadimitriou, G. and Lestas, M. and Pitsillides, A.},
year = {2012},
title = {{B}roadcast {S}cheduling with multiple concurrent costs},
pages = {178--186},
volume = {58},
number = {2},
journal = {IEEE Transactions on Broadcasting},
url = {./files/jrn/BTS1.pdf},
doi = {10.1109/TBC.2012.2191028}
}
@article{Liaskos.2012h,
author = {Liaskos, C. and Papadimitriou, G. and Nicopolitidis, P. and Pomportsis, A.},
year = {2012},
title = {{P}arallel {D}ata {B}roadcasting for {O}ptimal {C}lient {S}ervice {R}atio},
pages = {1741--1743},
volume = {16},
number = {11},
journal = {IEEE Communications Letters},
url = {./files/jrn/LCOMM.pdf},
doi = {LCOMM.2012.091212.1339}
}
@article{Abadal.2017,
author = {Abadal, Sergi and Liaskos, Christos and Tsioliaridou, Ageliki and Ioannidis, Sotiris and Pitsillides, Andreas and Sole-Pareta, Josep and Alarcon, Eduard and Cabellos-Aparicio, Albert},
year = {2017},
title = {Computing and Communications for the Software-Defined Metamaterial Paradigm: A Context Analysis},
journal = {IEEE Access},
pages = {1},
issn = {2169-3536},
doi = {10.1109/ACCESS.2017.2693267},
url = {./files/jrn/IEEEAccess17.pdf}
}
@inproceedings{LiaskosSTORE.2017,
author = {Liaskos, C. and Tsioliaridou, A. and Ioannidis, S.},
title = {The Socket Store: An App Model for the Application-Network Interaction},
booktitle={IEEE ISCC 2017},
doi = {10.1109/ISCC.2017.8024557},
articleabstract = {A developer of mobile or desktop applications is responsible for implementing the network logic of his software. Nonetheless: i) Developers are not network specialists, while pressure for emphasis on the visible application parts places the network logic out of the coding focus. Moreover, computer networks undergo evolution at paces that developers may not follow. ii) From the network resource provider point of view, marketing novel services and involving a broad audience is also challenge for the same reason. Moreover, the objectives of end-user networking logic are neither clear nor uniform. This constitutes the central optimization of network resources an additional challenge. As a solution to these problems, we propose the Socket Store. The Store is a marketplace containing end-user network logic in modular form. The Store modules act as intelligent mediators between the end-user and the network resources. Each module has a clear, specialized objective, such as connecting two clients over the Internet while avoiding transit networks suspicious for eavesdropping. The Store is populated and peer-reviewed by network specialists, whose motive is the visibility, practical applicability and monetization potential of their work. A developer first purchases access to a given socket module. Subsequently, he incorporates it to his applications under development, obtaining state-of-the-art performance with trivial coding burden. A full Store prototype is implemented and a critical data streaming module is evaluated as a driving case.},
url = {./files/cnf/ISCC17.pdf},
year = {2017}
}
@inproceedings{NN.2018,
author = {Pitilakis, A. and Tsilipakos, O. and Tasolamprou, A. and Liaskos, C. and Kantartzis, N. and. Economou, E. and Kafesaki, M. and Soukoulis, C.},
title = {Modeling and Simulation of Tunable Software-Defined Metasurfaces},
booktitle={The 15th International Conference on Nanosciences & Nanotechnologies (NN18)},
url = {./files/cnf/NN18.pdf},
year = {2018}
}
@inproceedings{SPECTS.2019,
author = {Mehrotra, R. and Ansari, R. I. and {Pitilakis, A., Nie, S.} and Liaskos, C. and Kantartzis, N. and Pitsillides., A.},
title = {3D Channel Modeling and Characterization for Hypersurface Empowered Indoor Environment at 60 GHz Millimeter-Wave Band},
booktitle = {Proceedings of IEEE SPECTS 2019},
year = 2019
}
@inproceedings{manosORCHESTRA.2017,
author = {Lakiotakis, E. and Liaskos, C. and Dimitropoulos, X.},
title = {Application-Network Collaboration using SDN for Ultra-Low Delay Teleorchestras},
booktitle={IEEE ISCC PEDISWESA Workshop 2017},
doi = {10.1109/ISCC.2017.8024507},
url = {./files/cnf/PEDISWESA17.pdf},
year = {2017},
articleabstract = {Networked Music Performance (NMP) constitutes a class of ultra-low delay sensitive applications, allowing geographically separate musicians to perform seamlessly as a tele-orchestra. For this application type, the QoS indicator is the mouth-to-ear delay, which should be kept under 25 milliseconds. The mouth-to-ear delay comprises signal processing latency and network delay. We propose a strong collaboration between the network and NMP applications to actively keep the to mouth-to-ear delay minimal, using direct state notifications. Related approaches can be characterized as passive, since they try to estimate the network state indirectly, based on the end application performance. Our solution employs Software Defined Networking (SDN) to implement the network-to-application collaboration, being facilitated by the well-defined network interface that SDN offers. Emulation results show that the proposed scheme achieves an improvement of up to 59% in mouth-to-ear delay over the existing passive solutions.}
}
@article{Liaskos:BTS,
author = {Liaskos, C. and Petridou, S. and Papadimitriou, G.},
year = {2010},
title = {{C}ost-{A}ware {W}ireless {D}ata {B}roadcasting},
pages = {66--76},
volume = {56},
number = {1},
journal = {IEEE Transactions on Broadcasting},
url = {./files/jrn/BTS.pdf},
doi = {10.1109/TBC.2009.2039521}
}
@article{Liaskos:TNET2019,
author = {Liaskos, C. and Tsioliaridou, A. and Nie, S. and Pitsillides, A. and Ioannidis, S. and Akyildiz, I.F.},
year = {2019},
title = {On the Network-layer Modeling and Configuration of Programmable Wireless Environments},
journal = {IEEE/ACM Transactions on Networking},
url = {./files/jrn/TNET2019.pdf}
}
@article{Liaskos:TVT,
author = {Liaskos, C. and Petridou, S. and Papadimitriou, G. and Nicopolitidis, P. and Pomportsis, A.},
year = {2010},
title = {{O}n the {A}nalytical {P}erformance {O}ptimization of {W}ireless {D}ata {B}roadcasting},
pages = {884--895},
volume = {59},
number = {2},
journal = {IEEE Transactions on Vehicular Technology},
url = {./files/jrn/TVT.pdf},
doi = {10.1109/TVT.2009.2035357}
}
@article{Liaskos:WCM,
author = {Liaskos, C. and Petridou, S. and Papadimitriou, G. and Nicopolitidis, P. and Pomportsis, A. and Obaidat, M.},
year = {2009},
title = {{C}lustering-driven {W}ireless {D}ata {B}roadcasting},
pages = {80--87},
volume = {16},
number = {6},
journal = {IEEE Wireless Communications Magazine},
url = {./files/jrn/WCM.pdf},
doi = {10.1109/MWC.2009.5361182}
}
@article{Liaskos.2012g,
author = {Liaskos, C. and Koutitas, G. and Vlahavas, I.},
year = {2012},
title = {{A} {H}olistic {V}irtual {L}aboratory on {W}ireless {C}ommunications and {S}ensor {N}etworks},
volume={7},
number={3},
pages={15--21},
journal = {International Journal of Interactive Mobile Technologies},
url = {./files/jrn/IJIM.pdf},
doi = {10.3991/2Fijim.v7i3.2480},
software = {./?Software#VLABS}
}
@article{Liaskos2014data,
title={On data compatibility and broadcast stream formation},
author={Liaskos, C. and Tsioliaridou, A. and Papadimitriou, G. and Nicopolitidis, P. and Pomportsis, A.},
journal={IEEE Transactions on Computers},
volume={63},
number={9},
pages={2369--2375},
year={2014},
publisher={IEEE},
url = {./files/jrn/TOC2.pdf},
doi = {10.1109/TC.2013.104}
}
@article{malindretos2014computer,
title={Computer assisted sound analysis of arteriovenous fistula in hemodialysis patients},
author={Malindretos, P. and Liaskos, C. and others},
journal={The International journal of artificial organs},
volume={37},
number={2},
pages={173--176},
year={2014},
url = {./files/jrn/IJAO.pdf},
doi = {10.5301/ijao.5000262},
keypoints = {To our knowledge this is the first attempt to use
computer assisted sound assessment for the estimation and analysis of the perceived bruit.
*computer assisted sound estimation is a readily available method that might increase
diagnostic accuracy, without adding expenses.},
articleabstract = {Traditionally, AVF function is assessed by clinical evaluation, Doppler ultrasound, Ultrasound dilution techniques,
venography, and dialysis adequacy methods (URR and Kt/V). Clinical examination represents the easiest method;
and is based on assessing a thrill and listening to the associated bruit at the site of arteriovenous anastomosis.
Even though this method is the easiest and most popular, it is subjective by definition and vastly dependent on
experience bias. The purpose of our study was to assess and analyze the produced bruit from blood circulation in
an AVF with the assist of a computerized method.}
}
@article{Liaskos2015promise,
title={A Promise of Realizable, Ultra-Scalable Communications at nano-Scale: A multi-Modal nano-Machine Architecture},
author={Liaskos, C. and Tsioliaridou, A.},
journal={IEEE Transactions on Computers},
volume={64},
number={5},
pages={1282--1295},
year={2015},
publisher={IEEE},
url = {./files/jrn/jrn_nano_TC.pdf},
doi = {10.1109/TC.2014.2329684}
}
@article{Tsioliaridou2016lightweight,
title={Lightweight, self-tuning data dissemination for dense nanonetworks},
author={Tsioliaridou, A. and Liaskos, C. and Ioannidis, S. and Pitsillides, A.},
journal={Nano Communication Networks (Special Issue on EM Nanonetworks)},
volume={8},
pages={2--15},
year={2016},
publisher={Elsevier},
url = {./files/jrn/NANOCOMNET.pdf},
doi = {10.1016/j.nancom.2015.09.003}
}
@article{Tsioliaridou2017comnet,
title={Packet Routing in 3D Nanonetworks: A Lightweight, Linear-path Scheme},
author={Tsioliaridou, A. and Liaskos, C. and Dedu, E. and Ioannidis, S.},
journal={Nano Communication Networks},
articleabstract={Packet routing in nanonetworks requires novel approaches, which can cope with
the extreme limitations posed by the nano-scale. Highly lossy wireless channels,
extremely limited hardware capabilities and non-unique node identifiers
are among the restrictions. The present work offers an addressing and routing
solution for static 3D nanonetworks that find applications in material monitoring
and programmatic property tuning. The addressing process relies on virtual
coordinates from multiple, alternative anchor point sets that act as viewports.
Each viewport offers different address granularity within the network space,
and its selection is optimized by a packet sending node using a novel heuristic.
Regarding routing, each node can deduce whether it is located on the linear
segment connecting the sender to the recipient node. This deduction is made
using integer calculations, node-local information and in a stateless manner,
minimizing the computational and storage overhead of the proposed scheme.
Most importantly, the nodes can regulate the width of the linear path, thus
trading energy efficiency (redundant transmissions) for increased path diversity.
This trait can enable future adaptive routing schemes. Extensive evaluation
via simulations highlights the advantages of the novel scheme over related approaches.},
volume={PP},
pages={PP},
year={2017},
publisher={Elsevier},
url = {./files/jrn/NANOCOMNET17.pdf},
doi = {10.1016/j.nancom.2017.01.001}
}
@article{Liaskos2015design,
title={Design and Development of Software Defined Metamaterials for Nanonetworks},
author={Liaskos, C. and Tsioliaridou, A. and Pitsillides, A. and Akyildiz, I. F. and Kantartzis, N. and Lalas, A. and Dimitropoulos, X. and Ioannidis, S. and Kafesaki, M. and Soukoulis, C.},
journal={IEEE Circuits and Systems Magazine},
volume={15},
number={4},
pages={12--25},
year={2015},
publisher={IEEE},
url = {./files/jrn/SDM1.pdf},
doi = {10.1109/MCAS.2015.2484098},
articleabstract={This paper introduces a class of programmable metamaterials, whose electromagnetic properties can be controlled via
software. These software defined metamaterials (SDMs) stem from utilizing metamaterials in combination with nanonetworks. Metamaterials
are artificial structures with properties that may not be found in nature. Since their initial advent, they have inspired ground-breaking
applications to a range of research topics, such as electromagnetic invisibility of objects (cloaking), radiation absorption, filtering
of light and sound as well as efficient antennas for sensors and implantable communication devices in recent years. However, existing
metamaterial structures are “rigid”, i.e. they cannot be restructured once constructed. This trait limits their fabrication to some well-
equipped laboratories worldwide, slows down innovation, and, most importantly, restricts their applicability to static structures only.
The proposed SDMs act as “plastic” (reconfigurable) metamaterials, whose attributes can be changed programmatically via a computer
interface. This control is achieved by a network of nanomachines, incorporated into the structure of the metamaterial. The nanomachines
may receive commands from the user and perform simple, yet geometrically-altering, actions on the metamaterial profile and tuning of its
electromagnetic behavior. Architectural aspects, expected features and implementation issues are covered in this paper, while a suitable
nanonetworking model is presented along with simulation results on its anticipated performance. The paper concludes by outlining the
research challenges pertaining to the analysis, design, prototyping, manufacturing, and initial application scenarios of the proposed
SDMs},
keypoints={The combination of metamaterials and nanonetworks can enable the programmatic control
over the electromagnetic behavior of matter.
*Metamaterials are artificially designed materials, with unnatural,
geometry-dependent electromagnetic properties.
*A network of nanomachines receives external, programmatic commands and performs geometry-altering actions,
yielding tunable or adaptive electromagnetic behavior.},
html={./?Publications___1-Page_reviews___IEEE_CAS&normal}
}
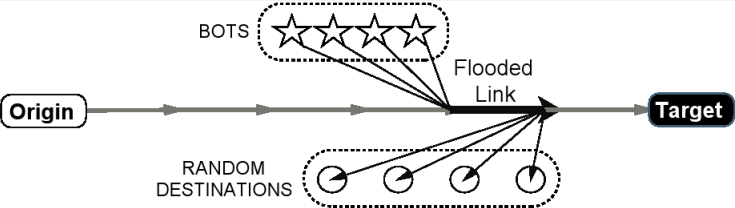
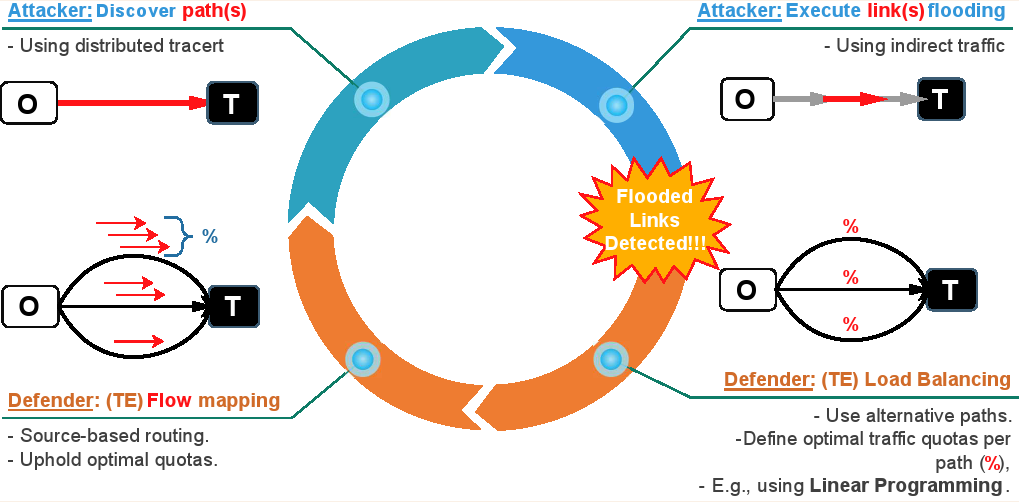
@article{gkounis2016interplay,
title={On the Interplay of Link-Flooding Attacks and Traffic Engineering},
author={Gkounis, D. and Kotronis, V. and Liaskos, C. and Dimitropoulos, X.},
journal={ACM SIGCOMM Computer Communication Review},
volume={46},
number={1},
pages={5--11},
year={2016},
publisher={ACM},
url = {./files/jrn/CCR16.pdf},
software = {./?Software#CCR},
doi = {10.1145/2935634.2935636},
articleabstract={Link-flooding attacks have the potential to disconnect even entire countries from the Internet. Moreover, newly
proposed indirect link-flooding attacks, such as “Crossfire”, are extremely hard to expose and, subsequently, mitigate effectively.
Traffic Engineering (TE) is the network’s natural way of mitigating link overload events, balancing the load and restoring connectivity.
This work poses the question: Do we need a new kind of TE to expose an attack as well? The key idea is that a carefully crafted, attack-
aware TE could force the attacker to follow improbable traffic patterns, revealing his target and his identity over time. We show that
both existing and novel TE modules can efficiently expose the attack, and study the benefits of each approach. We implement defense
prototypes using simulation mechanisms and evaluate them extensively on multiple real topologies.},
keypoints={Crossfire attacks can be exposed in a manner agnostic to the underlying, attack-unaware TE scheme.
*Certain attack-aware TE schemes can contain the effects of the attack within a small part of the network,
whereas attack-unaware TE may cause network-wide routing changes.},
html={./?Publications___1-Page_reviews___ACM_CCR}
}
@article{Liaskos.2011,
author = {Liaskos, C. and Xeros, A. and Papadimitriou, G. and Lestas, M. and Pitsillides, A.},
year = {2011},
title = {{B}alancing {W}ireless {D}ata {B}roadcasting and {I}nformation {H}overing for {E}fficient {I}nformation {D}issemination},
pages = {66--76},
volume = {58},
number = {1},
journal = {IEEE Transactions on Broadcasting},
url = {./files/jrn/BTS0.pdf},
doi = {10.1109/TBC.2011.2163449}
}
@article{Liaskos.2011d,
author = {Liaskos, C. and Papadimitriou, G.},
year = {2012},
title = {{E}ntropy-based estimation of client preferences in wireless push systems},
pages = {3899--3908},
volume = {60},
number = {12},
journal = {IEEE Transactions on Communications},
url = {./files/jrn/TCOMM.pdf},
doi = {TCOMM.2012.091712.110618}
}
@article{Liaskos.2012,
author = {Liaskos, C. and Papadimitriou, G.},
year = {2012},
title = {{G}eneralizing the {S}quare {R}oot {R}ule for {O}ptimal {P}eriodic {S}cheduling in {P}ush-based {W}ireless {E}nvironments},
journal = {IEEE Transactions on Computers},
pages = {1044--1050},
volume = {62},
number = {5},
url = {./files/jrn/TOC1.pdf},
doi = {10.1109/TC.2012.30}
}
@article{Liaskos2015minimal,
title={Minimal Wireless Broadcast Schedules for Multiobjective Pursuits},
author={Liaskos, C. and Tsioliaridou, A. and Papadimitriou, G. and Nicopolitidis, P.},
journal={IEEE Transactions on Vehicular Technology},
volume={64},
number={7},
pages={3098--3107},
year={2015},
publisher={IEEE},
url = {./files/jrn/TVT2.pdf},
doi = {10.1109/TVT.2014.2352399}
}
@article{kantelis2014use,
title={On the Use of FDTD and Ray-Tracing Schemes in the Nanonetwork Environment},
author={Kantelis, K. and Amanatiadis, S. and Liaskos, C. and Kantartzis, N. and Konofaos, N. and Nicopolitidis, P. and Papadimitriou, G.},
journal={IEEE Communications Letters},
volume={18},
number={10},
pages={1823--1826},
year={2014},
publisher={IEEE},
url = {./files/jrn/LCOMM1.pdf},
doi = {10.1109/LCOMM.2014.2355197}
}
@article{LiaskosCACM2018,
title={Using any Surface to Realize a New Paradigm for Wireless Communications},
author={Liaskos, C. and Tsioliaridou, A. and Pitsillides, A. and Ioannidis, S and Akyildiz, IF. },
journal={Communications of the ACM},
year = {2018},
publisher={ACM},
url = {./files/jrn/CACM18.pdf}
}
@article{LLiaskosWCM2018,
title={A New Wireless Communication Paradigm through Software-controlled Metasurfaces},
author={Liaskos, C. and Nie, S. and Tsioliaridou, A. and Pitsillides, A. and Ioannidis, S and Akyildiz, IF. },
journal={IEEE Communications Magazine},
year = {2018},
articleabstract = {Electromagnetic waves undergo multiple uncontrollable alterations as they propagate within a wireless environment. Free space path loss, signal absorption, as well as reflections, refractions and diffractions caused by physical objects within the environment highly affect the performance of wireless communications. Currently, such effects are intractable to account for and are treated as probabilistic factors. The paper proposes a radically different approach, enabling deterministic, programmable control over the behavior of the wireless environments. The key-enabler is the so-called HyperSurface tile, a novel class of planar meta-materials which can interact with impinging electromagnetic waves in a controlled manner. The HyperSurface tiles can effectively re-engineer electromagnetic waves, including steering towards any desired direction, full absorption, polarization manipulation and more. Multiple tiles are employed to coat objects such as walls, furniture, overall, any objects in the indoor and outdoor environments. An external software service calculates and deploys the optimal interaction types per tile, to best fit the needs of communicating devices. Evaluation via simulations highlights the potential of the new concept.},
url = {./files/jrn/COMMAG18.pdf}
}
@inproceedings{LiaskosWOWOMOM2018,
author = {Liaskos, C. and Nie, S. and Tsioliaridou, A. and Pitsillides, A. and Ioannidis, S and Akyildiz, IF. },
title = {Realizing Wireless Communication through Software-defined HyperSurface Environments},
booktitle = {IEEE WoWMoM'18},
year = {2018},
articleabstract = {Wireless communication environments are unaware of the ongoing data exchange efforts within them. Moreover, their effect on the communication quality is intractable in all but the simplest cases. The present work proposes a new paradigm, where indoor scattering becomes software-defined and, subsequently, optimizable across wide frequency ranges. Moreover, the controlled scattering can surpass natural behavior, exemplary overriding Snell's law, reflecting waves towards any custom angle (including negative ones). Thus, path loss and multi-path fading effects can be controlled and mitigated. The core technology of this new paradigm are metasurfaces, planar artificial structures whose effect on impinging electromagnetic waves is fully defined by their macro-structure. The present study contributes the software-programmable wireless environment model, consisting of several HyperSurface tiles controlled by a central, environment configuration server. HyperSurfaces are a novel class of metasurfaces whose structure and, hence, electromagnetic behavior can be altered and controlled via a software interface. Multiple networked tiles coat indoor objects, allowing fine-grained, customizable reflection, absorption or polarization overall. A central server calculates and deploys the optimal electromagnetic interaction per tile, to the benefit of communicating devices. Realistic simulations using full 3D ray-tracing demonstrate the groundbreaking potential of the proposed approach in 2.4 GHz and 60 GHz frequencies.},
url = {./files/cnf/WoWMoM18.pdf}
}
@inproceedings{LiaskosNOCARC2018,
author = {Saeed, T. and Skitsas, D. and others},
title = {Fault Adaptive Routing in Metasurface Controller Networks},
booktitle = {NocArc'18},
year = {2018},
articleabstract = {HyperSurfaces are a merge of structurally reconfigurable
metasurfaces whose electromagnetic properties can be
changed via a software interface, using an embedded miniaturized
network of controllers, thus enabling novel capabilities in
wireless communications. Resource constraints associated with
the development of a hardware testbed of this breakthrough
technology necessitate network controller architectures different
from traditional regular Network-on-Chip architectures. The
Manhattan-like topology chosen to realize the controller network
in the testbed under development is irregular, with restricted
local path selection options, operating in an asynchronous
fashion. These characteristics render traditional fault-tolerant
routing mechanisms inadequate. In this paper, we present work
in progress towards the development of fault-tolerant routing
mechanisms for the chosen architecture. We present two XYbased
approaches which have been developed aiming to offer
reliable data delivery in the presence of faults. The first approach
aims to avoid loops while the second one attempts to maximize the
success delivery probabilities. Their effectiveness is demonstrated
via simulations conducted on a custom developed simulator.},
url = {./files/cnf/NOCARC18.pdf}
}
@article{Liaskos2016service,
title={Service Ratio-Optimal, Content Coherence-Aware Data Push Systems},
author={Liaskos, C. and Tsioliaridou, A.},
journal={ACM Transactions on Management Information Systems},
volume = {6},
number = {4},
year = {2016},
pages = {1--23},
publisher={ACM},
url = {./files/jrn/TMIS1.pdf},
doi = {10.1145/2850423}
}
@article{Tsioliaridou2015captcha,
title={Fast and Fair Handling of Multimedia CAPTCHA Flows},
author={Tsioliaridou, A. and Zhang, C. and Liaskos, C.},
journal={International Journal of Interactive Mobile Technologies},
volume={9},
number={4},
year={2015},
pages={1-4},
url = {./files/jrn/IJIM1.pdf},
doi = {10.3991/ijim.v9i4.4644}
}
@article{Tsioliaridou2015fastfair,
title={On the Fair Handling of TCP Flows},
author={Tsioliaridou, A. and Zhang, C. and Liaskos, C. and Tsaoussidis, V.},
journal={International Journal of Communication Networks and Distributed Systems},
volume={TBA},
number={TBA},
year={2016},
pages={1-14},
url = {./files/jrn/IJCNDS16.pdf}
}
@inproceedings{Liaskos.2008,
author = {Liaskos, C. and Petridou, S. and Papadimitriou, G. and Nicopolitidis, P. and Obaidat, M. and Pomportsis, A.},
title = {{A} {N}ovel {C}lustering - {D}riven {A}pproach to {W}ireless {D}ata {B}roadcasting},
pages={1-6},
booktitle = {IEEE SCVT'08},
year = {2008},
url = {./files/cnf/SCVT08.pdf}
}
@inproceedings{Yiannopoulos.2013,
author = {Yiannopoulos, K. and others},
title = {PANDA: Asymmetric Passive Optical Network for xDSL and FTTH Access},
booktitle = {PCI'13},
year = {2013},
pages = {335--342},
numpages = {8},
url = {http://users.ics.forth.gr/cliaskos/files/cnf/PCI2013.pdf},
doi = {10.1145/2491845.2491885},
publisher = {ACM}
}
@inproceedings{Liaskos.2009,
author = {Liaskos, C. and Petridou, S. and Papadimitriou, G.},
title = {{A} new approach to the design of wireless data broadcasting systems: {A}n analysis-based cost-effective scheme},
pages = {1--8},
isbn = {978-1-4244-3942-3},
booktitle = {IEEE ICUMT'09},
year = {2009},
url = {./files/cnf/ICUMT2009.pdf},
doi = {10.1109/ICUMT.2009.5345463}
}
@inproceedings{Liaskos.2009b,
author = {Liaskos, C. and Petridou, S. and Papadimitriou, G. and Nicopolitidis, P. and Pomportsis, A.},
title = {{A}n analytical approach to the design of wireless broadcast disks systems},
pages = {1--8},
isbn = {978-1-4244-4327-7},
booktitle = {IEEE ISADS'09},
year = {2009},
url = {./files/cnf/ISADS2009.pdf},
doi = {10.1109/ISADS.2009.5207371}
}
@inproceedings{Liaskos.2010b,
author = {Liaskos, C. and Petridou, S. and Papadimitriou, G.},
title = {{C}ombining optimal performance with cost-efficiency in adaptive wireless broadcast-based systems},
pages = {1221--1226},
publisher = {IEEE},
isbn = {978-1-4244-5793-9},
booktitle = {IEEE MELECON'10},
year = {2010},
url = {./files/cnf/MELECON2010.pdf},
doi = {10.1109/MELCON.2010.5475915}
}
@inproceedings{Liaskos.2011b,
author = {Liaskos, C. and Xeros, A. and Papadimitriou, G. and Pitsillides, A.},
title = {{I}nformation hovering: {A} new approach for performance acceleration of wireless push systems},
pages = {809--814},
booktitle = {IEEE ISCC'11},
year = {2011},
url = {./files/cnf/ISCC2011.pdf},
doi = {10.1109/ISCC.2011.5983941}
}
@inproceedings{Liaskos.2011c,
author = {Liaskos, C. and Papadimitriou, G.},
title = {{M}inimizing mean client serving time and broadcast schedule cost in wireless push systems},
pages = {1--6},
booktitle = {IEEE BMSB'11},
year = {2011},
url = {./files/cnf/BMSB2011.pdf},
doi = {10.1109/BMSB.2011.5954928}
}
@inproceedings{Liaskos.2012c,
author = {Liaskos, C. and Xeros, A. and Papadimitriou, G. and Pitsillides, A.},
title = {{P}eriodic {S}cheduling with {C}osts: {A} {N}ovel {A}pproach to {W}ireless {D}ata {B}roadcasting},
pages = {52--63},
booktitle = {WWIC'12},
year = {2012},
url = {./files/cnf/wwic2012.pdf},
doi = {10.1007/978-3-642-30630-3_5}
}
@inproceedings{Liaskos.2012d,
author = {Liaskos, C. and Tsioliaridou, A. and Papadimitriou, G.},
title = {{M}ore for {L}ess: {G}etting more clients by broadcasting less data},
pages = {64--75},
booktitle = {WWIC'12},
year = {2012},
url = {./files/cnf/WWIC2012b.pdf},
doi = {10.1007/978-3-642-30630-3_6}
}
@inproceedings{Liaskos:SCVT10,
author = {Liaskos, C. and Papadimitriou, G.},
title = {{U}ltra lightweight adaptation processes for scheduling {S}ervers in {P}ush-based {S}ystems},
pages = {1--6},
booktitle = {IEEE SCVT'10},
year = {2010},
url = {./files/cnf/SCVT2010.pdf},
doi = {10.1109/SCVT.2010.5720465}
}
@inproceedings{Malindretos.2011,
author = {Malindretos, P. and Liaskos, C. and others},
title = {{S}ound {A}ssessment and {S}ound {A}nalysis of {A}rteriovenous {F}istula ({A}{V}{F}) in {H}emodialysis {P}atients},
booktitle = {The {X}{L}{V}{I}{I}{I} ERA-EDTA Congress},
year = {2011},
pages ={1-6},
url = {./files/cnf/ERAEDTA11.pdf},
doi = {10.13140/RG.2.1.4186.5049},
keypoints = {To our knowledge this is the first attempt to use
computer assisted sound assessment for the estimation and analysis of the perceived bruit.
*computer assisted sound estimation is a readily available method that might increase
diagnostic accuracy, without adding expenses.},
articleabstract = {Traditionally, AVF function is assessed by clinical evaluation, Doppler ultrasound, Ultrasound dilution techniques,
venography, and dialysis adequacy methods (URR and Kt/V). Clinical examination represents the easiest method;
and is based on assessing a thrill and listening to the associated bruit at the site of arteriovenous anastomosis.
Even though this method is the easiest and most popular, it is subjective by definition and vastly dependent on
experience bias. The purpose of our study was to assess and analyze the produced bruit from blood circulation in
an AVF with the assist of a computerized method.}
}
@inproceedings{Liaskos.2012b,
author = {Liaskos, C. and Koutitas, G. and Vlahavas, I.},
title = {{V}irtual {L}aboratories on {W}ireless {C}ommunications: {A} {C}ontemporary, {E}xtensible {A}pproach},
pages = {1--10},
booktitle = {IEEE EDUCON'12},
year = {2012},
url = {./files/cnf/EDUCON12.pdf},
doi = {10.1109/EDUCON.2012.6201078},
software = {./?Software#VLABS}
}
@inproceedings{Liaskos.2013,
author = {Liaskos, C. and Papadimitriou, G. and Douligeris, C.},
title = {Sensor Swarm Query Filtering: Heightened Attack Resilience for Broadcast on-Demand Services},
year = {2013},
pages = {1-6},
booktitle = {IEEE ISCC'13},
publisher = {IEEE},
url = {./files/cnf/ISCC2013.pdf},
doi = {10.1109/ISCC.2013.6754965}
}
@inproceedings{samaras2015enhancing,
title={Enhancing the Trustworthiness of Service On-Demand Systems via Smart Vote Filtering},
author={Samaras, C. and Tsioliaridou, A. and Liaskos, C. and Spiliotopoulos, D. and Ioannidis, S.},
booktitle={Springer TRUST'15},
pages={88--103},
year={2015},
url = {./files/cnf/TRUST2015.pdf},
doi = {10.1007/978-3-319-22846-4_6}
}
@inproceedings{Liaskos2015lightweight,
title={A lightweight, non-intrusive approach for orchestrating autonomously-managed network elements},
author={Liaskos, C.},
booktitle={IEEE ISCC'15},
pages={335--340},
year={2015},
organization={IEEE},
url = {./files/cnf/ISCC15.pdf},
ppt={./files/ppt/BPTE.pptx},
doi = {10.1109/ISCC.2015.7405537}
}
@inproceedings{Tsioliaridou2015corona,
title={CORONA: A Coordinate and Routing system for Nanonetworks},
author={Tsioliaridou, A. and Liaskos, C. and Ioannidis, S. and Pitsillides, A.},
booktitle={ACM NANOCOM'15},
pages={18},
year={2015},
url = {./files/cnf/NANOCOM15.pdf},
doi = {10.1145/2800795.2800809}
}
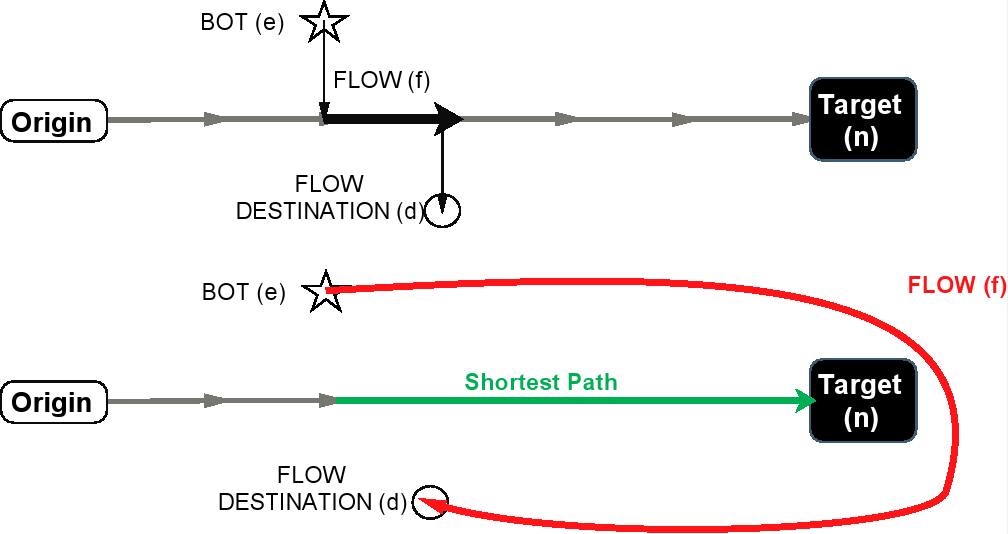
@inproceedings{Liaskos2016novel,
title={A Novel Framework for Modeling and Mitigating Distributed Link Flooding Attacks},
author={Liaskos, C. and Kotronis, V. and Dimitropoulos, X.},
year={2016},
booktitle={IEEE INFOCOM'16},
pages={1-9},
url = {./files/cnf/INFOCOM16.pdf},
doi = {10.1109/INFOCOM.2016.7524507},
ppt = {./files/ppt/INFCM16.pdf},
software = {./?Software#INFOCOM},
html= {./?Publications___1-Page_reviews___IEEE_INFOCOM%2716&normal},
articleabstract={Distributed link-flooding attacks constitute a new class of attacks with the
potential to segment large areas of the Internet. Their distributed nature makes detection and
mitigation very hard. This work proposes a novel framework for the analytical modeling and optimal
mitigation of such attacks. The detection is modeled as a problem of relational algebra,
representing the association of potential attackers (bots) to potential targets. The analysis seeks
to optimally dissolve all but the malevolent associations. The framework is implemented at the
level of online Traffic Engineering (TE), which is naturally triggered on link-flooding events. The
key idea is to continuously re-route traffic in a manner that makes persistent participation to
link-flooding events highly improbable for any benign source. Thus, bots are forced to adopt a
suspicious behavior to remain effective, revealing their presence. The load-balancing objective of
TE is not affected at all. Extensive simulations on various topologies validate our analytical
findings.},
keypoints={Introduced a novel framework for studying stealthy DDoS link-flooding attacks.
*Goal: Facilitate detection of susceptible bots and targets.
*Use relational algebra to formulate bot-to-target area relations.
*Benefit: Ease and scalability of implementation (via standard SQL).
*Our entry point: the Traffic Engineering (TE) process.
*Use same inputs, leave TE load-balancing objectives untouched.
*Detection-optimal mapping of flows-to-paths.
*Key idea: keep probable bots targets at separate paths, then punish persistence.}
}
@inproceedings{Liaskosdeployable,
title={A Deployable Routing System for Nanonetworks},
author={Liaskos, C. and Tsioliaridou, A. and Ioannidis, S. and Kantartzis, N. and Pitsillides, A.},
year={2016},
booktitle={IEEE ICC'16},
pages={1-6},
url = {./files/cnf/ICC16.pdf},
doi = {10.1109/ICC.2016.7511151},
html = {./?Publications___1-Page_reviews___IEEE_ICC%2716&normal},
articleabstract={Nanonetworks comprise numerous wireless nodes, assembled at micro-to-nano scale.
The unique manufacturing challenges and cost considerations of these networks make for minimal
complexity solutions at all network layers. From a networking aspect, packet retransmissions should
be kept minimal, while ensuring communication between any two nanonodes. In addition, assigning
unique addresses to nanonodes is not straightforward, since it can entail a prohibitively high
number of packet exchanges. Thus, efficient data routing is considered an open issue in
nanonetworking. The present paper proposes a routing system which can be dynamically deployed
within a nanonetwork. Static, dense topologies with numerous, identical nodes are examined. These
attributes are especially important in the context of recently proposed applications of
nanonetworks. The proposed scheme incurs a trivial setup overhead and requires integer processing
capabilities only. Once deployed, it operates efficiently, inducing lower packet retransmission
rates than related schemes.},
keypoints={This study introduced a deployable routing system (DEROUS) for ad hoc nanonetworks.
*DEROUS dynamically forms a quasi-radial coordinate system around a given beacon point.
*Emphasis is placed on low complexity and memory requirements.
*Each node is assumed to have integer processing capabilites only.}
}
@inproceedings{Tsioliaridou1n3,
title={N3: Addressing and Routing in 3D Nanonetworks},
author={Tsioliaridou, A. and Liaskos, C. and Pachis, L. and Ioannidis, S. and Pitsillides, A.},
booktitle={IEEE ICT'16},
year={2016},
pages={1-6},
url = {./files/cnf/ICT16.pdf},
doi = {10.1109/ICT.2016.7500372},
bpa = {},
html = {./?Publications___1-Page_reviews___IEEE_ICT%2716&normal},
articleabstract={Wireless communication at nanoscale faces unique challenges stemming from low
hardware capabilities, limited power supply and unreliable channel conditions. The present paper
proposes a networking scheme that can operate efficiently under such physical restrictions.
Studying 3D multi-hop networks, the novel scheme offers scalable, trilateration-based node
addressing and low-complexity packet routing mechanisms. Analysis is employed to design a routing
process that balances path multiplicity for robust data delivery, and minimization of redundant
transmissions. Extensive simulations yield increased resilience to challenging network conditions.},
keypoints={A nanonetwork addressing and routing scheme is proposed, named N3.
*N3 provides path multiplicity and node failover, which are mandatory in the challenging nano-environment.
*A triplet of anchors is selected by a sender-node prior to its transmission.
*Each triplet selection yields a different boudning volume, allowing for optimization of selection.
*N3 was optimized analytically in terms of minimization of retransmissions,
whilst ensuring the high resilience of the network demanded by many applications,
e.g. smart materials. }
}
@inproceedings{Tsioliaridou2015SLR,
title={Stateless Linear-path Routing for 3D Nanonetworks},
author={Tsioliaridou, A. and Liaskos, C. and Dedu, E. and Ioannidis, S.},
booktitle={ACM NANOCOM'16},
year={2016},
pages={1-6},
url = {./files/cnf/NANOCOM16.pdf},
html = {./?Publications___1-Page_reviews___ACM_NANOCOM%2716&normal},
articleabstract={Efficient data routing is a critical enabler of future
nanonetworking applications. Such nano-routing schemes must account for highly lossy
wireless channel conditions, non-unique identifiers and limited processing capabilities
at the nanonodes comprising the network. The present study proposes a novel addressing
and routing scheme fit for 3D nanonetworks. Initially, a geo-addressing process is
applied within the network. Subsequently, it is shown that every node can deduce whether
it is located on the linear path connecting a communicating node-pair. This deduction
is made using integer calculations, node-local information and in a stateless manner,
minimizing the computational and storage overhead of the proposed scheme. Most importantly,
the nodes can regulate the width of the linear path, thusly trading energy efficiency
(redundant transmissions) for increased path diversity. This trait can enable future
adaptive routing schemes. Extensive evaluation via simulations highlights the advantages
of the novel scheme over related approaches.},
ppt={./files/ppt/ACMNanoCom2016.pdf},
doi={10.1145/2967446.2967451},
keypoints={Multi-hop nano-networks have interesting applications (active metamaterials).
*Multi-hop adds another networking restriction, i.e., low manufacturing cost per node.
*This is captured by assuming weak nano-node CPUs (integer-processing only) and limited RAM.
*The proposed Stateless, Linear Routing (SLR) is an effective solution for node addressing and
packet routing with tunable path redundancy.
*Key-enabler of SLR is the use of curvilinear coordinates.},
ideas={Due to curvilinearity, straight lines get distorted and bent.
But the distortion differs in significance.
Lines near our anchor viewport get bent more,
while lines further back remain straight.
Define the optimal anchors per sender-receiver pair, that minimizes the distortion degree.
*Virtual Coordinates suffer from resolution degradation: large areas too far from viewpoints
share the same coordinates. This may favor node fail-over, but can hamper energy efficiency.
Study the trade-off between curvilinearity and address resolution when selecting a viewpoint.
}
}
@inproceedings{meta2016,
title={Modified Perfectly Matched Layers in Finite-Difference Time-Domain Schemes for the Efficient Truncation of Propagating Graphene Surface Waves (poster)},
author={Amanatiadis, S. and Liaskos, C. and Kafesaki, M. and Kantartzis, N.},
booktitle={METAMATERIALS'16},
year={2016},
pages={1-2},
url = {./files/cnf/META16.pdf}
}
@misc{Liaskos.2013j3.1,
author = {Liaskos, C.},
title = {A Crossfire Attack Simulator},
howpublished = {Computer software},
software = {./?Software#CCR},
year = {2016}
}
@misc{Liaskos.MedSoft.2014,
author = {Malindretos, P. and Liaskos, C.},
year = {2014},
title = {Using software to assess the status of arteriovenous fistulae},
howpublished = {Computer software},
url = {http://www.tech.ihu.edu.gr/index.php/en/research/item/30-virtual-labs.html},
software = {./?Software&normal#fistulaSOFT}
}
@misc{Liaskos.2013k3.1,
author = {Liaskos, C.},
year = {2016},
title = {A Software Platform for Evaluating Crossfire Attack Mitigation Schemes},
howpublished = {Computer software},
software = {./?Software#INFOCOM}
}
@misc{Liaskos.IHU,
author = {Liaskos, C. and Koutitas, G.},
year = {2011},
title = {Virtual Labs: Wireless Telecommunication and Sensor Networks},
howpublished = {Computer software},
url = {http://www.tech.ihu.edu.gr/index.php/en/research/item/30-virtual-labs.html},
software = {./?Software#VLABS}
}
@article{Liaskos.2013j3,
title={Backpressure on the Backbone: A Lightweight, Non-intrusive Traffic Engineering Approach},
author={Liaskos, C. and Dimitropoulos, X. and Tassiulas, L.},
journal={IEEE Transactions on Network and Service Management},
volume={14:1},
pages={176--190},
year={2016},
publisher={IEEE},
doi={10.1109/TNSM.2016.2631477},
url = {./files/jrn/TNSM1.pdf},
articleabstract={The present study proposes a novel collaborative traffic engineering
scheme for networks of autonomous systems. Backpressure routing principles
are used for deriving priority routing rules that optimally stabilize
a network, while maximizing its throughput under latency considerations.
The routing rules are deployed to the network following simple SDN
principles. The proposed scheme requires minimal, infrequent interaction
with a central controller, limiting its imposed workload. Furthermore,
it respects the internal structure of the autonomous systems and their
existing peering relations. In addition, it co-exists smoothly with
underlying distance vector-based routing schemes. The proposed scheme
combines simplicity with substantial gains in served transit traffic
volume, as shown by simulations in realistic setups and proven via
mathematical analysis.},
keypoints={A minimal-commitment/high-gain collaboration scheme may be
required to convince Autonomous Systems to try-out central orchestration.
*Applying Back-pressure (BPR) routing within a group of ASes can constitute
the basis for such a collaboration scheme.
*BPR promises throughput optimality, resulting in increased transit traffic,
fair distribution of additional traffic, increased network stability and
resilience to congestion events.
*BPR is simple in its operation and requires no changes in hardware,
BGP operation or peering policy violation.},
html={./?Publications___1-Page_reviews___IEEE_TNSM}
}
Make sure you write within the PRE!
 )
)